Before I chat your ears off, can you quickly go and subscribe to my page? I’m really trying to make this blog grow! Have you ever heard of a hi-jack within a hi-jack? Well, this new exploit is called account pre-hijacking. It sounds funky, but Cyber T is going to elucidate this topic for your understanding. I didn’t even know my brain could come up with words like that. I think that deserves a round of applause you know.
Fun fact: ain’t nothing fun about hijacking accounts
Back to the topic, account pre-hijacking is when an attacker signs up to a service using your email address in order to gain more of your personal data. You’re probably wondering how an attacker managed to get your e-mail address? Well, in the world of cybersecurity there’s a term called ‘data dumps’, this is when a website has a data breach and loads of e-mail addresses are published on the dark web.
There are different ways in which a pre-hijacking can work. Ultimately, it all boils down to the fact that some services do not authenticate the user when signing up. There are two ways to sign into a service, either email and password or via Google/Facebook.
When you reset your password it should ask you to sign in again. However, there is a vulnerability that does not sign you out even if you’ve reset your password. Attackers use this to their advantage and still remain logged in to your account even after you have reset the password.
Another way pre-hijacking works is by the following infographic:
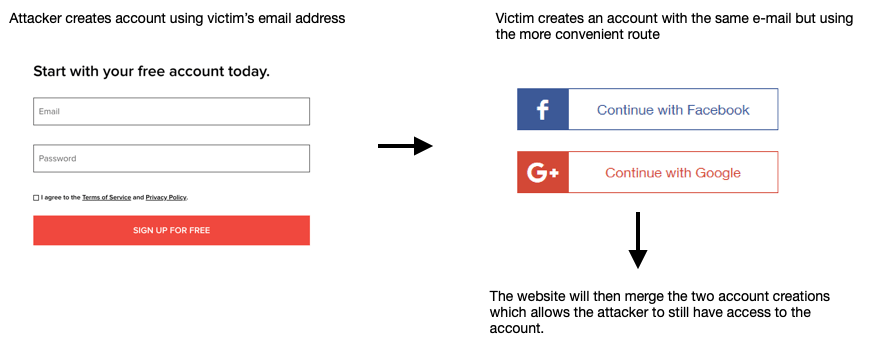
Have you ever tried to sign up to a service but it says that your e-mail address is already registered? I’m 98% sure that it’s not a hacker but that’s basically what you’ll see when trying to create an account. If you were to reset the password, the attacker may still be able to have access to the account using that e-mail address. To be 100% sure, I’d suggest using a different e-mail as this will prevent the attack altogether. You can also use two-factor authentication to prevent the attacker authenticating the hi-jacked account.
Security researchers have found that Zoom, Instagram (again), LinkedIn and my beloved WordPress were affected by this vulnerability. Thankfully, they have all sorted this issue out, so we’re all bless. Nevertheless, I do feel as though it’s important to know what type of attacks are out there and to understand how much work attackers are putting into finding gaps in security.
Love & Guidance
TT

Makes sense! Thanks for letting us know. So next time I see an already registered sign, I know who to track
LikeLike