Find me one start-up company that doesn’t have integrity as one of their company values. It’s a good quality to have and it’s very vital in the world of information security. In the last blog we looked at the ‘C’ in the CIA triad and how it’s implemented. Let’s now take a look at the ‘I’ in the triad.
Integrity is the assurance that the data stored on your system has not been edited or deleted by a person who has no permission to do so, or doing so without permission. If this was to occur, that means a data breach can easily materialise.
Do you remember the scene in Power when Angela deletes Tasha’s gun from the FBI database whilst using someone else’s login credentials? This is an example of a violation of integrity where data has been deleted without permission. To be honest the FBI need to have better processes in place as it was way too simple for the data to be deleted. I would suggest implementing the 4-eyed principle or having a ‘segregation of duties’ process in place, but I guess it’s a TV show and not an accurate depiction.
Let me not digress, but you can imagine the dangers of this. Imagine your health records being altered and your medical notes are suggesting you’ve been diagnosed with something that you don’t have, or that you need a certain medicine that you don’t need.
I mentioned in the last blog that the health care sector needs to ensure compliance and follow the guidelines of the HIPAA (Health Insurance Portability and Accountability Act) as they hold patient health data.
There are different ways in which integrity is implemented:
Checksum is used to verify that data has not been tampered with. See the following infographic below:
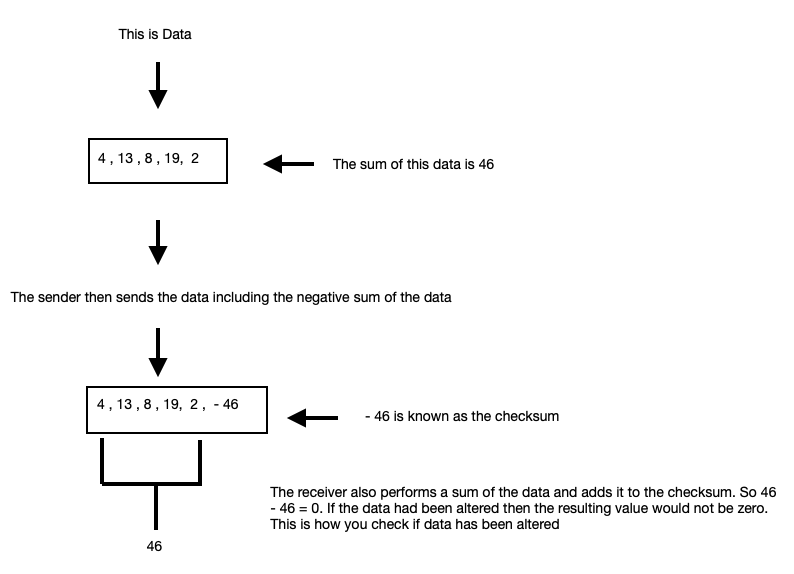
Segregation of duties ensures that more than one person is needed to complete a task, so if you were to edit data, that action would need to be approved by someone else. This reduces the chance of an accidental change or deletion. It also reduces the chance of a deliberate alteration. (I hope the FBI are reading this point)
The 4 eyes principle requires that two individuals approve an action before it is taken. Human error is a factor that can cause a breach in data integrity as data is sometimes accidentally deleted or edited. This principle ensures that there is another set of eyes to remove the possibility of a mistake.
Collaboration is another method to ensure integrity. Let’s use the example of SharePoint, it’s a collaboration tool which shows who has edited the document or even deleted the document. Not even Peter could deny that he made the changes.
It’s important to understand that cybersecurity is a journey rather than a destination and that there are a lot of concepts within the protection of data so I hope that the way I’ve explained them has made sense. In the next blog I’ll cover the ‘A’ part of the CIA triad.
Love & Guidance
TT
