Encryption is used to protect our e-mails, sensitive information, and those online purchases we want to keep hush hush. It also helps protect the data we receive and store on our devices. So, How does encryption work?
Well, encryption will take plain text and then use an algorithm to scramble it into ciphertext. Once the intended party accesses the message, the message is translated back to its original form which is called decryption. For example, plain text = How are you but when encrypted, will look something like this: ciphertext = bgs lhc ugd. This protects sensitive information by making it hard for hackers to understand what was originally sent.
Ciphertext goes way back to Julius Caesar’s day and he was known to have used this method to send messages to his army generals and his concubines (Yeah, Uncle J wasn’t only invading countries). As one of the simplest forms of encryption, substitution method is where the alphabet is shifted 3 spaces and a letter is replaced by another in that position. This would turn a normal message into a random string of letters and could only be deciphered by people who knew the technique.
For example:
| Plain | A | B | C | D | E |
| Cypher | X | Y | Z | A | B |
Encryption Systems
There are two types of encryption systems: symmetric and asymmetric. Symmetric is where one key is used to encrypt and decrypt data. For example, if I send a password-protected document to a person, I would also need to send the password so they can open the document.
Asymmetric uses a public key to encrypt the data which is shared, and a private key to decrypt the data which is not shared. For example, I use my recipient’s public key which they shared, to encrypt the document. I would then send the document to them and they will use their private key to decrypt it. Only the intended recipient can decrypt this document unless their private key has been compromised.
Interesting things about Encryption
In my last blog I spoke about HTTPS and this protocol uses SSL asymmetric encryption. SSL (Secure Sockets Layer) is used to provide communications security i.e emails, instant messaging and wi-fi calls over the network. When we are shopping online be sure to check if the website link begins with HTTPS rather than HTTP. Also, look to see if there is a padlock icon in the URL as this is a sign that the website is encrypted.
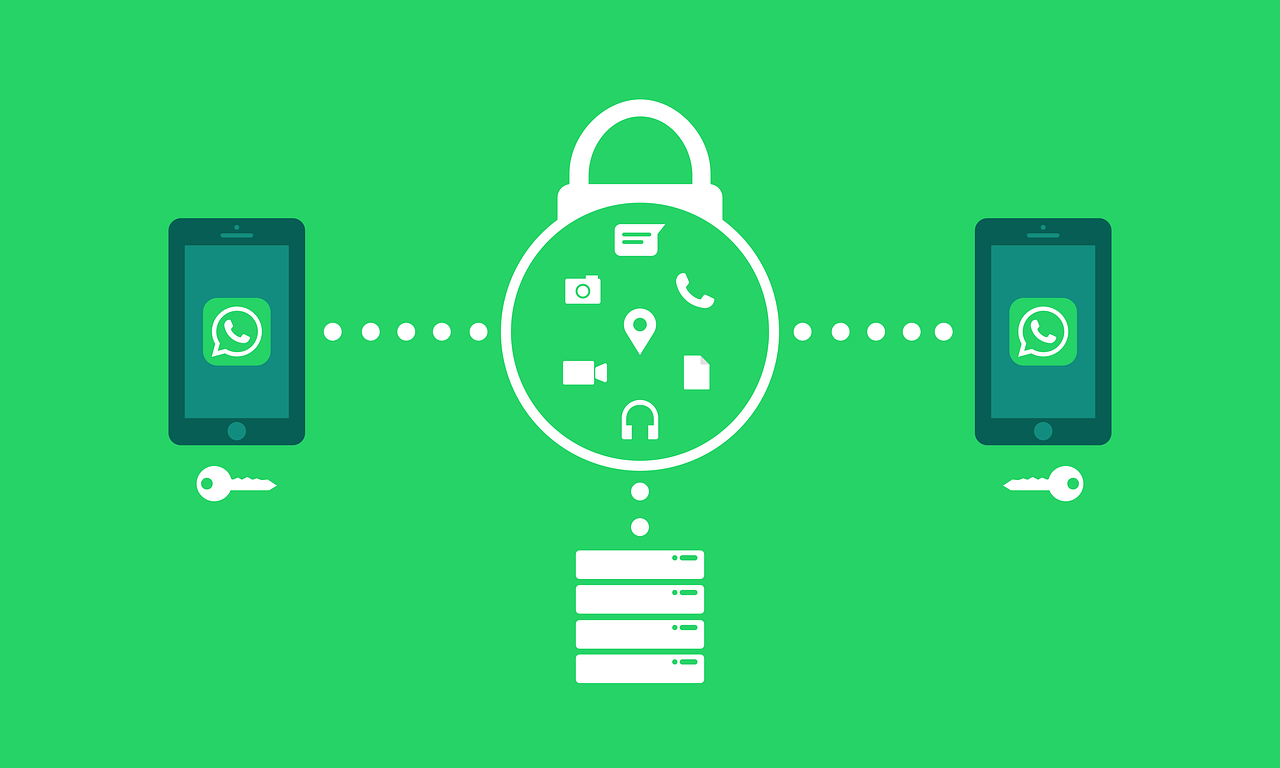
We all use WhatsApp, but did you know that WhatsApp has end-to-end encryption available? End-to-end encryption means only you and the person you are messaging can read what is being sent, so nobody, not even WhatsApp or the government can read your message. A lot of apps that have the messenger feature do not use end-to-end encryption, so they can not guarantee protection.
There are other interesting methods of sending protected messages. Steganography is the art of hiding a secret message within an ordinary message or file. Stegosuite is an online tool you can use to embed messages into GIFs and JPEG images and send it to your mates. They will also need the tool to extract your message (my Twitter DM’s are gonna be different now boy, not that it wasn’t popping before).
Encryption helps protect our online privacy by ensuring our personal information is only seen by the people that need to see them. So let’s make sure we check to see if the mediums we use to send private information have the right encryption methods in place. Encryption is very complex topic and this is just the first few pieces to the puzzle.
| Tips with T |
| – Always check that the padlock icon appears in the URL when shopping online – Always check to see if the website link is using HTTPS |
PSA *Blasts Horn* – CHALLENGE TIME, LET’S GOOOO !!!
This week I’ll be giving away a £100 cash prize for whoever can decipher the following text:
“ Xlivi mw rs tvmdi “
To send in your answer, fill in the ‘Contact Us’ page below. .
Get CRACKING !!!
Love & Guidance
TT
Contact Us
Loooool this guy is too much
LikeLiked by 1 person
That was an insightful read once again!
LikeLiked by 1 person
I want to win this!
LikeLike
Awesome read like always, keep them coming
LikeLike
Very interesting, there is certain platforms that I have used before for encryption like Google mailvelope, to send encrypted emails or encrypted documents. But didn’t know it was used during Julius Caesar’s days.
LikeLike
Proper good read. These encryption techniques could help me get back into Mi5 🤔
LikeLike
Very nice article and I love the way it was conveyed.
LikeLike
Very insightful, I look forward to the next one.
LikeLike